3. Conducting Cloud Security Assessments
Ensuring cloud security requires regular vulnerability assessments and compliance checks across various cloud providers. This guide outlines the procedures to assess security posture in AWS, Azure, and Microsoft Security (M365 & Entra ID).
Cloud Security – AWS Security
- Log In to the Security Portal
-
Enter your credentials (username and password) to access the Security Portal.
-
- Navigate to Cloud Security
-
Open the Side Navigation Bar on the left.
-
Click on the Cloud Security tab to access security tools.
-
- Select AWS Security
-
Click on AWS Security to view available scanning options.
-
- Verify AWS Account
-
Ensure that an AWS account is linked through the Integrations page.
-
If missing, add the AWS account before proceeding.
-
- Choose a Compliance Standard
-
Select a compliance framework to evaluate security posture:
-
CIS (Center for Internet Security)
-
PCI DSS v3.2.1 (Payment Card Industry Data Security Standard)
-
GDPR (General Data Protection Regulation)
-
SOC2 (System and Organization Controls 2)
-
-
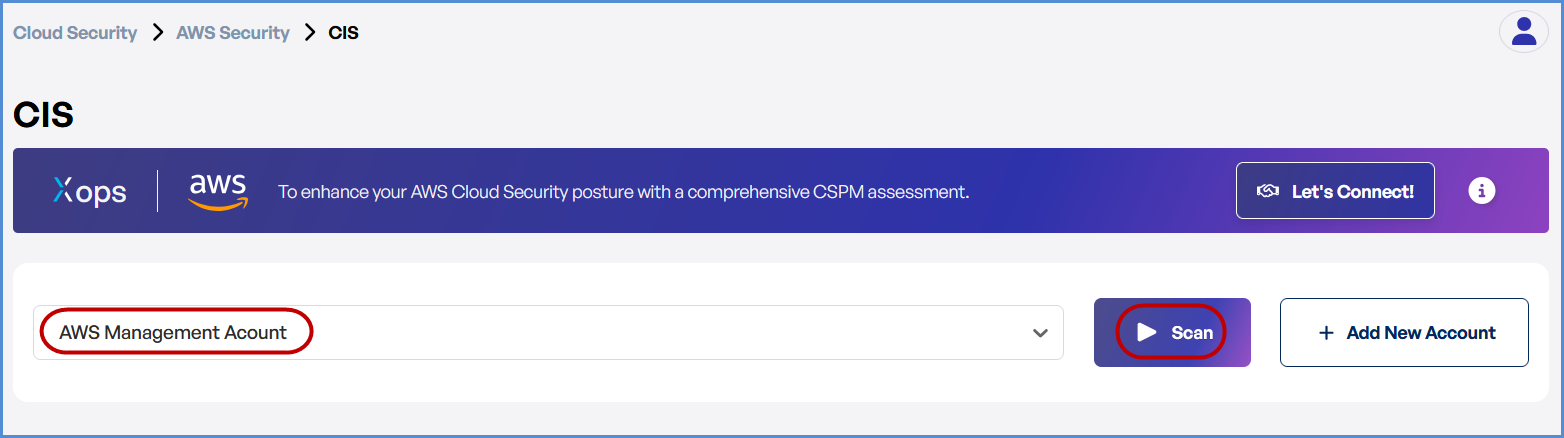
- Initiate the Scan
-
Locate the AWS account under the selected compliance framework.
-
Click Scan to initiate an automated security check.
-
Monitor and Review Results
-
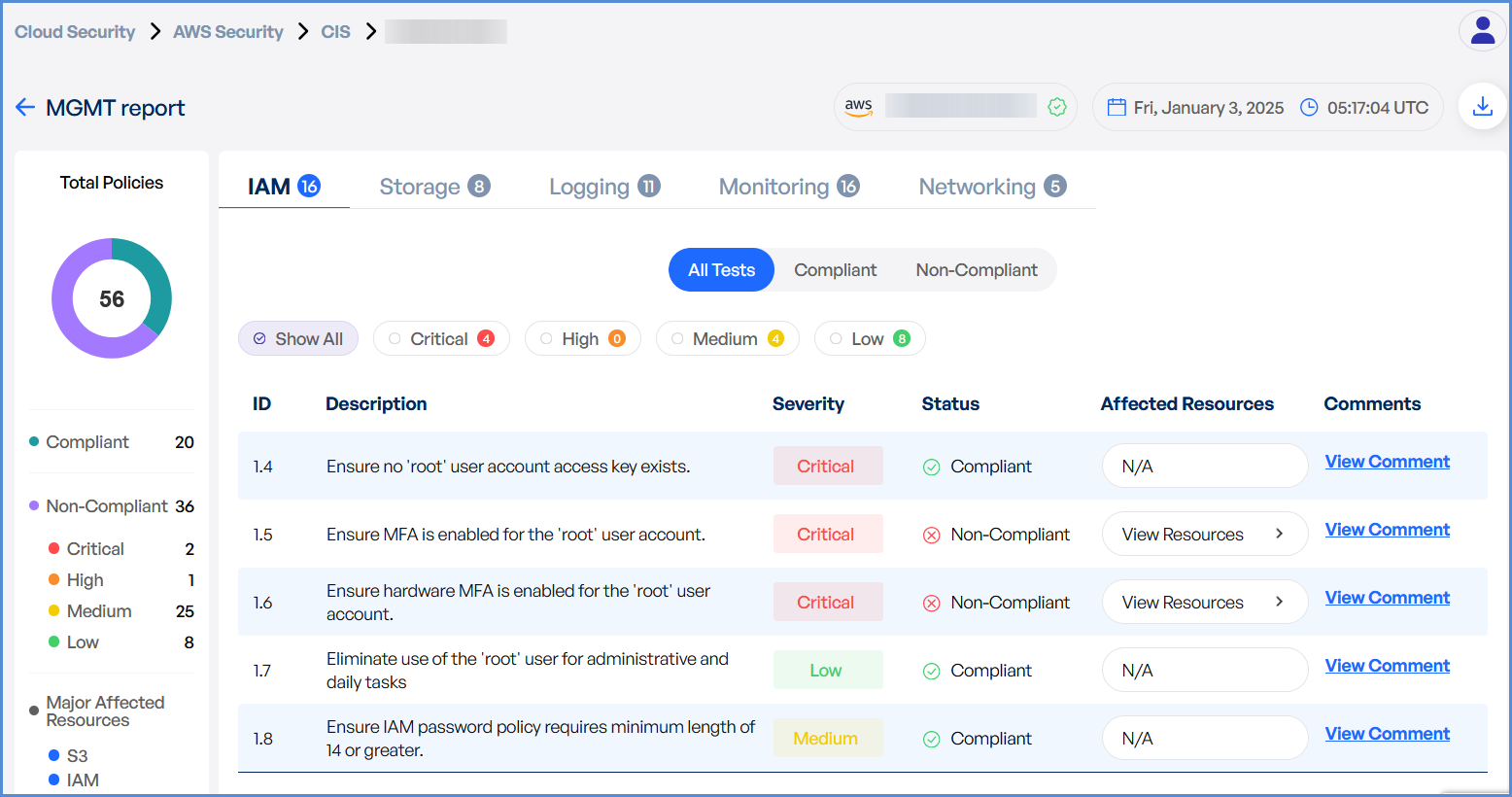
Monitor scan progress, and upon completion, a report will be generated then open it.
-
Review findings, including:
-
Compliance gaps
-
Security misconfigurations
-
Vulnerabilities
-
Cloud Security – Azure Security
- Log In to the Security Portal
-
Enter your credentials to log in.
-
- Navigate to Cloud Security
-
Open the Side Navigation Bar and select Cloud Security.
-
- Select Azure Security
-
Click Azure Security to access scan options.
-
- Verify Azure Account
-
Ensure an Azure account is added via the Integrations page.
-
If missing, add an account before proceeding.
-
- Choose a Compliance Standard
-
Select a compliance framework for the security assessment:
-
ISO (International Organization for Standardization)
-
SOC2 (System and Organization Controls 2)
-
CIS (Center for Internet Security)
-
-
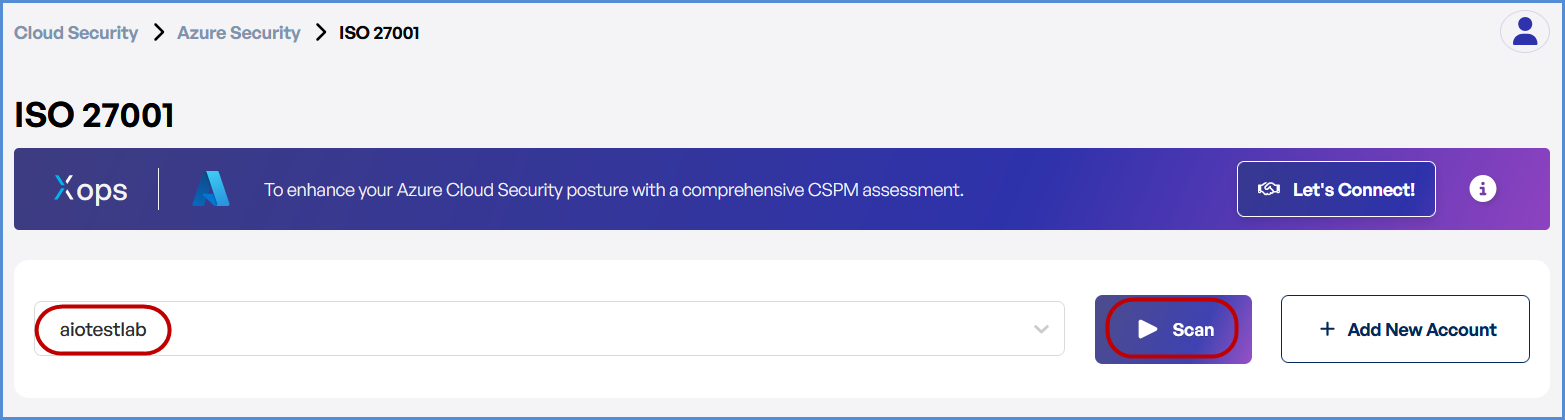
- Initiate the Scan
-
Locate the Azure account under the selected compliance framework.
-
Click Scan to start the security analysis.
-
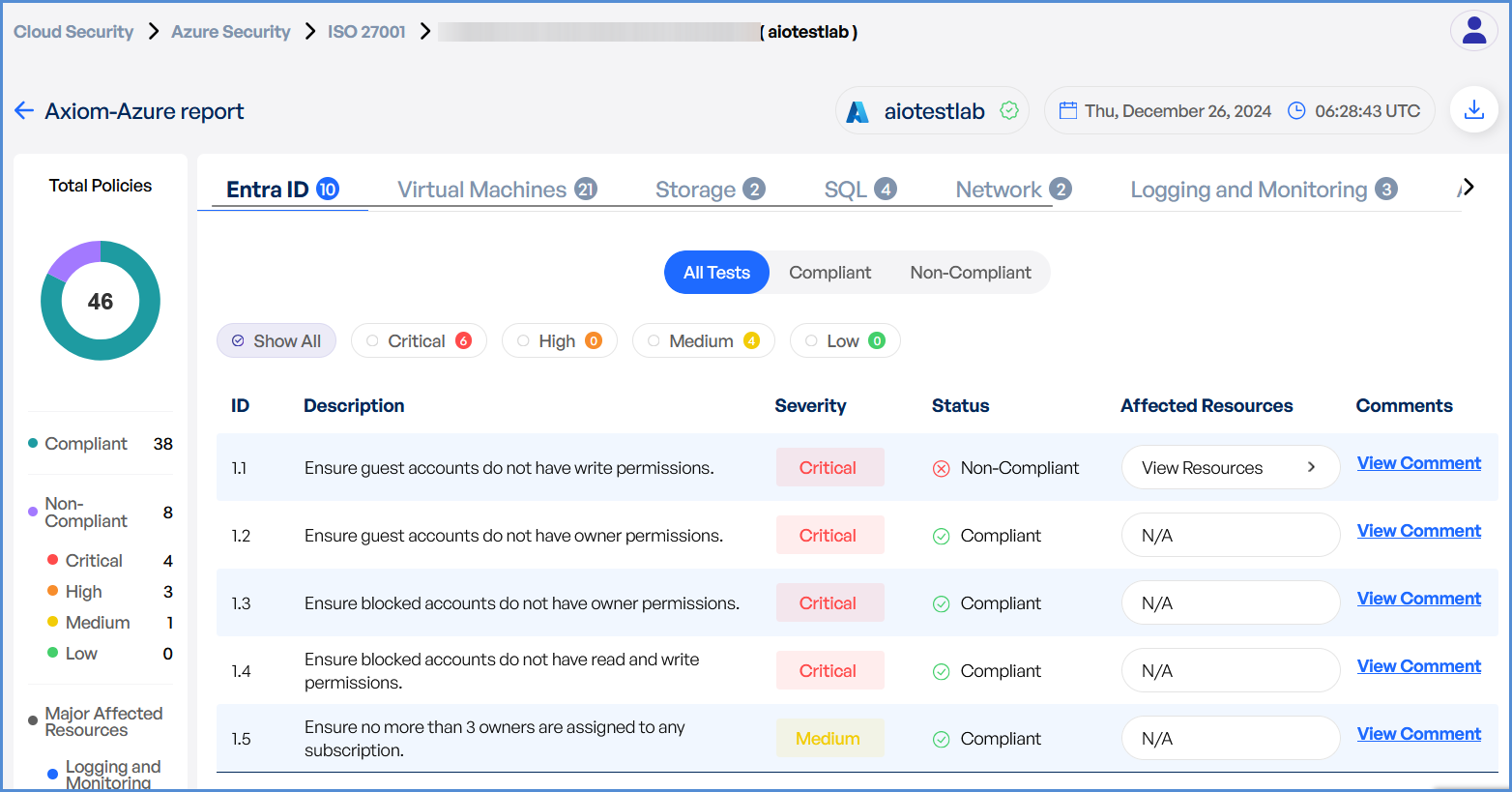
Monitor and Review Results
-
View scan progress on the Cloud Security Dashboard.
-
Analyze scan results to detect:
-
Compliance gaps
-
Security misconfigurations
-
Vulnerabilities
-